
Cellphones of two outstanding human rights activists had been repeatedly focused with Pegasus, the extremely superior spy ware made by Isreal-based NSO, researchers from Amnesty Worldwide reported this week.
The Moroccan human rights defenders acquired SMS textual content messages containing hyperlinks to malicious websites. If clicked, the websites would try to put in Pegasus, which as reported here and here, is likely one of the most superior and full featured items of spy ware ever to return to mild. One of many activists was additionally repeatedly subjected to assaults that redirected visits supposed for Yahoo to malicious websites. Amnesty Worldwide recognized the targets as activist Maati Monjib and human rights lawyer Abdessadak El Bouchattaoui.
Serial pwner
It’s not the primary time NSO spy ware has been used to surveil activists or dissidents. In 2016, United Arab Emirates dissident Ahmed Mansoor acquired textual content messages that attempted to lure him to a web site that will install Pegasus on his fully patched iPhone. The positioning relied on three separate zeroday vulnerabilities in iOS. In accordance with earlier reviews from Univision, Amnest International, and University of Toronto-based Citizen Lab, NSO spy ware has additionally focused:
- 150 folks, together with US residents and opposition critics chosen by an ex-president of Panama
- 22 journalists and activists researching corruption within the Mexican authorities
- Two folks—one an Amnesty Worldwide researcher and the opposite a dissident—in Saudi Arabia
This week’s report mentioned that the concentrating on of the 2 Morrocan human rights defenders started no later than November 2017 and certain lasted till at the very least July of this 12 months. In 2017 and 2018, the boys acquired textual content messages that contained hyperlinks to websites together with stopsms[.]biz and infospress[.]com, which Amnesty Worldwide previously said was part of NSO’s exploit infrastructure. Different domains included revolution-news[.]co, which Citizen Lab has identified as tied to NSO, and the beforehand unknown hmizat[.]co, which seems to impersonate Moroccan ecommerce firm Hmizate.
Suspicious redirects
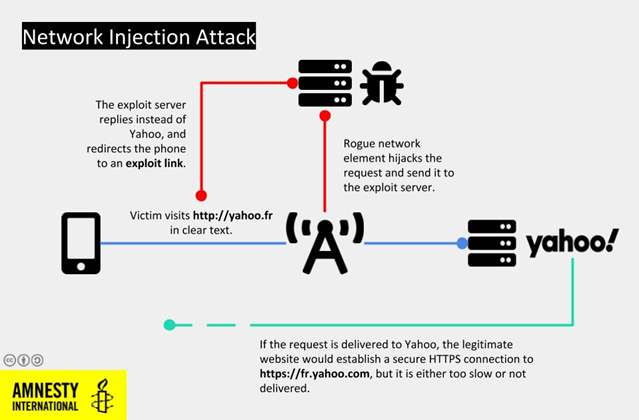
Then, beginning this 12 months, Monjib’s iPhone began being suspiciously redirected to malicious websites. An evaluation of logs Safari shops of every visited hyperlink and the origin and vacation spot of every go to confirmed the redirects occurred after Monjib entered “yahoo.fr“ within the tackle bar of his Safari browser. Below regular circumstances, Safari would rapidly be redirected to the encrypted hyperlink https://fr.yahoo.com/. However on at the very least 4 events, from March of this 12 months to July, the activist was as an alternative diverted to hyperlinks together with
hxxps://bun54l2b67.get1tn0w.free247downloads[.]com:30495/szev4hz
and
hxxps://bun54l2b67.get1tn0w.free247downloads[.]com:30495/szev4hz#048634787343287485982474853012724998054718494423286
.
These redirections had been presumably solely as a result of the preliminary connection to Yahoo wasn’t protected by an encrypted HTTPS connection. Within the redirection from July, Monjib once more tried to entry Yahoo, however as an alternative of typing an tackle within the browser, he looked for “yahoo.fr mail” on Google. When he clicked the consequence, he landed on the proper web site. Authors of this week’s report wrote:
We imagine it is a symptom of a community injection assault usually known as “man-in-the-middle” assault. Via this, an attacker with privileged entry to a goal’s community connection can monitor and opportunistically hijack visitors, resembling internet requests. This permits them to vary the behaviour of a focused system and, resembling on this case, to re-route it to malicious downloads or exploit pages with out requiring any additional interplay from the sufferer.
Such a community vantage level could possibly be any community hop as shut as potential to the focused system. On this case, as a result of the focused system is an iPhone, connecting by way of a cell line solely, a possible vantage level could possibly be a rogue mobile tower positioned within the proximity of the goal, or different core community infrastructure the cell operator might need been requested to reconfigure to allow this sort of assault.
As a result of this assault is executed “invisibly” by way of the community as an alternative of with malicious SMS messages and social engineering, it has the benefits of avoiding any consumer interplay and leaving nearly no hint seen to the sufferer.
We imagine that is what occurred with Maati Monjib’s telephone. As he visited yahoo.fr, his telephone was being monitored and hijacked, and Safari was mechanically directed to an exploitation server which then tried to silently set up spy ware.
Amnesty Worldwide
Amnesty Worldwide researchers mentioned they imagine at the very least one of many injections “was profitable and resulted within the compromise of Maati Monjib’s iPhone." The researchers continued:
At any time when an utility crashes, iPhones retailer a log file preserving traces of what exactly induced the crash. These crash logs are saved on the telephone indefinitely, at the very least till the telephone is synced with iTunes. They are often present in Settings > Privateness > Analytics > Analytics Information. Our evaluation of Maati Monjib’s telephone confirmed that, on one event, all these crash information had been wiped a couple of seconds after considered one of these Safari redirections occurred. We imagine it was a deliberate clean-up executed by the spy ware with a view to take away traces that would result in the identification of the vulnerabilities actively exploited. This was adopted by the execution of a suspicious course of and by a compelled reboot of the telephone.
A preponderance of proof
The researchers mentioned they will’t show the redirections had been the work of NSO services or products, however they are saying proof strongly suggests a hyperlink. The proof consists of similarities between the identified NSO URLs contained within the SMS messages—resembling
hxxps://videosdownload[.]co/nBBJBIP
and the URLs used within the redirects —resembling
hxxps://bun54l2b67.get1tn0w.free247downloads[.]com:30495/szev4hz
. Each are composed of generic domains adopted by a pseudorandom alphanumeric string of seven to 9 characters.
The researchers additionally discovered the same community injection functionality described in a doc titled Pegasus—Product Description that was discovered within the 2015 hack of NSO competitor Hacking Team. The NSO doc calls the redirect functionality a “Tactical Community Aspect” and describes how a rogue cell tower could possibly be used to determine a focused telephone and remotely inject and set up Pegasus.
Amid rising criticism, NSO Group—which earlier this 12 months was valued at $1 billion in a leveraged buyout by UK-based personal fairness agency Novalpina Capital—promised in September to observe a human rights coverage primarily based on these guiding principles. A key facet of the coverage was to “examine at any time when the corporate turns into conscious of alleged illegal digital surveillance and communication interception of NSO merchandise.”
In a response to this week’s report, NSO officers wrote:
As per our coverage, we examine reviews of alleged misuse of our merchandise. If an investigation identifies precise or potential hostile impacts on human rights, we're proactive and fast to take the suitable motion to deal with them. This will likely embody suspending or instantly terminating a buyer’s use of the product, as we've achieved up to now.
Whereas there are important authorized and contractual constraints regarding our skill to touch upon whether or not a specific authorities company has licensed our merchandise, we're taking these allegations significantly and can examine this matter in step with our coverage. Our merchandise are developed to assist the intelligence and legislation enforcement neighborhood save lives. They aren't instruments to surveil dissidents or human rights activists. That’s why contracts with all of our prospects allow using our merchandise solely for the legit functions of stopping and investigating crime and terrorism. If we ever uncover that our merchandise had been misused in breach of such a contract, we'll take applicable motion.
In an e mail, an NSO consultant mentioned applicable motion may embody shutting down a buyer’s entry to the NSO system, which the corporate has achieved 3 times up to now.
Amnesty Worldwide, for its half, stays skeptical.
“Within the absence of sufficient transparency on investigations of misuse by NSO Group and due diligence mechanisms, Amnesty Worldwide has lengthy discovered these claims spurious,” this week’s report mentioned. “With the revelations detailed on this report, it has turn out to be more and more apparent that NSO Group’s claims and its human rights policy are an try and whitewash rights violations induced by way of its merchandise.”
