
Attackers exploited a zeroday vulnerability in Apple's iTunes and iCloud packages to contaminate Home windows computer systems with ransomware with out triggering antivirus protections, researchers from Morphisec reported on Thursday. Apple patched the vulnerability earlier this week.
The vulnerability resided within the Bonjour part that each iTunes and iCloud for Home windows depends on, in accordance with a blog post. The bug is called an unquoted service path, which as its title suggests, occurs when a developer forgets to encompass a file path with citation marks. When the bug is in a trusted program—akin to one digitally signed by a widely known developer like Apple—attackers can exploit the flaw to make this system execute code that AV safety would possibly in any other case flag as suspicious.
Morphisec CTO Michael Gorelik defined it this manner:
As many detection options are primarily based on conduct monitoring, the chain of course of execution (parent-child) performs a significant position in alert constancy. If a legit course of signed by a identified vendor executes a brand new malicious baby course of, an related alert could have a decrease confidence rating than it will if the dad or mum was not signed by a identified vendor. Since Bonjour is signed and identified, the adversary makes use of this to their benefit. Moreover, safety distributors attempt to reduce pointless conflicts with identified software program functions, so they won't forestall this behaviorally for worry of disrupting operations.
Unquoted path vulnerabilities have been present in different packages, together with an Intel graphics driver, the ExpressVPN, and the Forcepoint VPN.
In August, Morphisec discovered attackers have been exploiting the vulnerability to put in ransomware known as BitPaymer on the computer systems of an unidentified firm within the automotive business. The exploit allowed the attackers to execute a malicious file known as "Program," which presumably was already on the goal's community.
Gorelik continued:
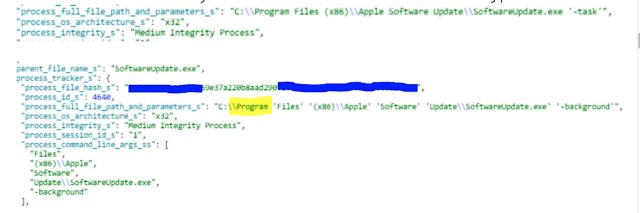
Moreover, the malicious "Program" file does not include an extension akin to ".exe". This implies it's doubtless that AV merchandise is not going to scan the file since these merchandise are likely to scan solely particular file extensions to restrict the efficiency affect on the machine. On this state of affairs, Bonjour was making an attempt to run from the "Program Recordsdata" folder, however due to the unquoted path, it as a substitute ran the BitPaymer ransomware because it was named "Program". That is how the zero-day was capable of evade detection and bypass AV.
Gorelik stated that Morphisec "instantly" notified Apple of the lively exploit upon discovering it in August. On Monday, Apple patched the vulnerability in each iTunes 12.10.1 for Windows and iCloud for Windows 7.14. Home windows customers who've both utility put in ought to guarantee the automated updates labored as they're purported to. In an electronic mail, Gorelik stated his firm has reported further vulnerabilities that Apple has but to patch. Apple representatives did not reply to an electronic mail looking for remark for this put up.
What's extra, anybody who has ever put in and later uninstalled iTunes ought to examine their PCs to make sure Bonjour was additionally eliminated. That is as a result of the iTunes uninstaller does not robotically take away Bonjour.
"We have been shocked by the outcomes of an investigation that confirmed the Bonjour updater is put in on numerous computer systems throughout totally different enterprises," Gorelik wrote. "Most of the computer systems uninstalled iTunes years in the past whereas the Bonjour part stays silently, un-updated, and nonetheless working within the background."
An apart: Gorelik described Bonjour as "a mechanism that Apple makes use of to ship future updates." Apple and plenty of different sources, in the meantime, say it is a service Apple functions use to search out shared music libraries and different sources on an area community. In an electronic mail, Gorelik stated Bonjour serves each capabilities.
"Furthermore within the particular assault, Bonjour was executing the SoftwareUpdate executable that's situated beneath C:Program Recordsdata (x86)Apple Software program UpdateSoftwareUpdate.exe, however as a substitute they executed C:Program with the remainder as parameters -> "C:Program 'Recordsdata' '(x86)Apple' 'Software program' 'UpdateSoftwareUpdate.exe,'" he wrote. He went on to say that Apple builders "have not mounted all of the vulnerabilities reported by us, solely the one which was abused by the attackers."
